Blogger:
Instagram: lucifer_man_
Botnets:-
Definition:
Botnet attack is of a propelled sort whereby the assaulted PC framework turns into an attacker itself. This causes genuine worries in the IT world which ought to be known to each framework head and senior innovation the executives.
Explain:
The word botnet is gotten from the expression “system of robots”. It is basically a far reaching accumulation of countless tainted PC frameworks. Each tainted framework runs a bit of programming project called as a “Bot”.
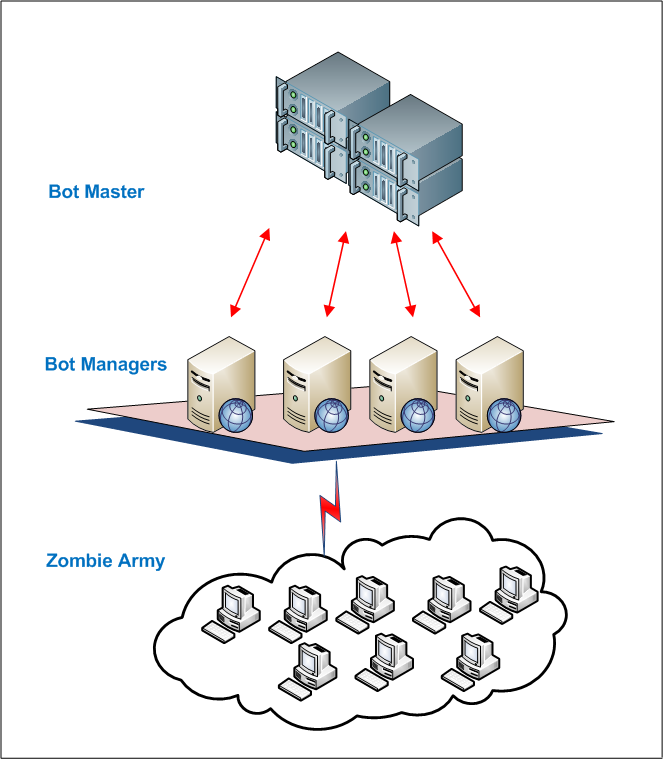
As appeared in Figure 1., there is a Bot-Master framework which monitors all out number of machines tainted and the undertakings they ought to perform. For painstakingly arranged frameworks, which need organization between a huge number of such frameworks, another layer of Bot-Managers is made as well. Bot-Managers play out the assignments to acknowledge directions from the ace, to spread out those directions to the bots and furthermore to report the quantity of frameworks contaminated under its ward. The chief botnets are additionally seen as sending refreshed programming patches to fix bugs or improve usefulness, fundamentally the
same as a security fix administration framework. The Bot-Master is responsible for the programmer who has underhanded goals to make this military. Anyway since the programmer should escape getting captured, the ace frameworks and programming running on it are continually working in a stealth mode. In couple of present day botnet assaults, the botmasters were found to designate and pivot the ace’s job between its botmanagers, along these lines making it incredibly extreme to distinguish. These job changes were additionally seen as turning their proprietorship dependent on the nation of quality, so as to guarantee immense infractions over the globe. Typically botnets are intended for a particular working framework, and if a more extensive spread must be accomplished, botnets incline toward web code, or java language, to taint all the conceivable working framework stages.
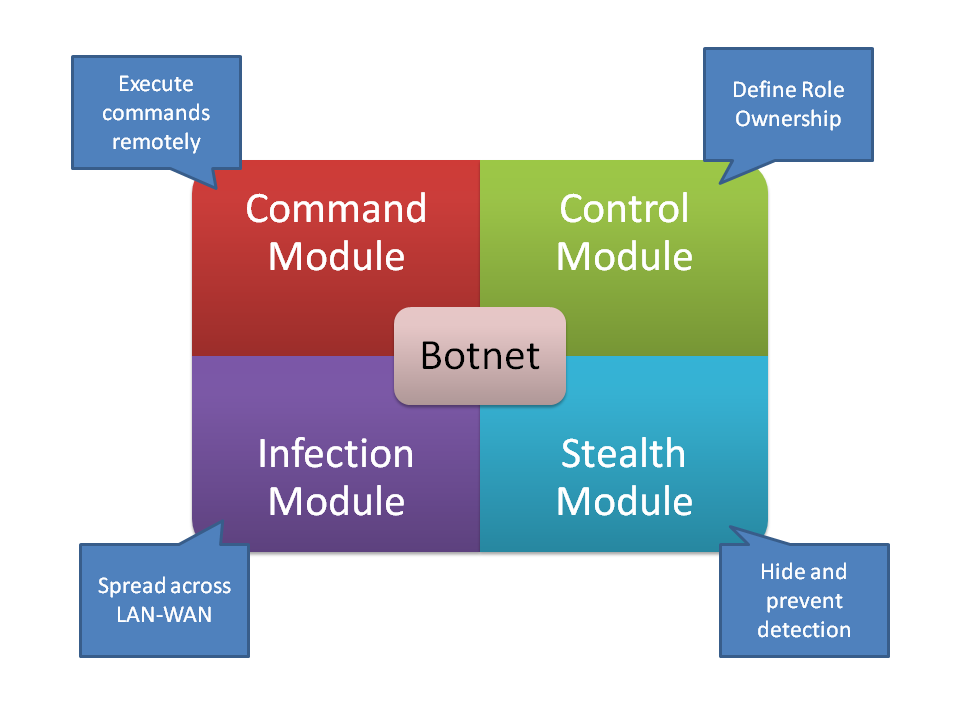
Presently how about we investigate the interior tasks of a commonplace Bot. As appeared in Figure 2., there are 4primary modules of a botnet. Direction module
 sends directions to the youngster botnets, while the control module controls the proprietorships, to choose who ought to tune in to whom. The disease module conveys significant duty of discovering non-fixed servers in the system and contaminating those with the most refreshed duplicate. The stealth module is basically a lot of programming programs which does the significant activity, for example, incapacitating antivirus; accomplish root access or part get to. It additionally guarantees that its very own impression on the tainted machine is imperceptible as far as running procedures and circle space, and furthermore keeps a watch on new antivirus programming being introduced. At times, the stealth module and control module cooperate to bring a latest fix of itself from the ace or chief, and consistently overhauls itself. Some stealth modules are likewise fit for deleting themselves utilizing a fall to pieces component or shutdown the framework, to ruin the forceful recognition systems.
sends directions to the youngster botnets, while the control module controls the proprietorships, to choose who ought to tune in to whom. The disease module conveys significant duty of discovering non-fixed servers in the system and contaminating those with the most refreshed duplicate. The stealth module is basically a lot of programming programs which does the significant activity, for example, incapacitating antivirus; accomplish root access or part get to. It additionally guarantees that its very own impression on the tainted machine is imperceptible as far as running procedures and circle space, and furthermore keeps a watch on new antivirus programming being introduced. At times, the stealth module and control module cooperate to bring a latest fix of itself from the ace or chief, and consistently overhauls itself. Some stealth modules are likewise fit for deleting themselves utilizing a fall to pieces component or shutdown the framework, to ruin the forceful recognition systems.
The way botnets associate with the ace or administrator is fascinating as well. All bots are given an exceptional distinguishing proof number, which is generally a result of the tainted framework’s design and area, however not really the ip address of the framework. The ace consistently has a most refreshed tally of these distinguishing proof numbers utilized, and is fit for restricting the spread or grow it. Bots utilize a particular scope of TCP ports; anyway the precise port being utilized is gotten arbitrarily. It is consistently the obligation of the botnet itself to report the TCP port number it intends to use, to the ace or chief. This announcing happens upon each reboot of the tainted framework. Much of the time the between Bot interchanges are base-64 or md5 encoded, while at times a self marked computerized declaration is seen as utilized as well.
The principle reason behind infusing a botnet into a framework is to make a multitude of tainted frameworks, additionally called as zombie machines. The table underneath clarifies different sorts of botnets and the reason behind infusing those into a system. The general reason behind such an assault is at last, to upset PC frameworks or to take information. Since an entire armed force of PC zombies are in real life, tragically the programmer can undoubtedly and rapidly prevail in his abhorrent crucial, is on the grounds that planting a botnet assault is constantly an okay, high benefit work.
How Botnets are infused:
In beginning of web, a botnet code piece was created to automatically navigate through numerous sites and to further assemble and group the substance to make significant information. While this strategy shapes the core of the present web crawlers, it was changed previously by programmers to their advantages. Before we talk about how botnets are infused, we should comprehend why it is finished. To put a site on the map in an internet searcher, it is basic to get heaps of web demands. This is particularly valid for sites which show commercials and procure cash for each snap on a distributed promotion. It is conceivable to spread botnets over the systems, to get to the website page and automatically click at least one commercials on it. On the off chance that such a battle is deliberately arranged, it is hard to make sense of which snap is started by an individual truly, and which one is beginning from a botnet code. The site facilitating individual, generally a programmer in such a case, can wind up winning bunches of cash. In another assortment called as phishbots, an email crusade can be begun to accomplish comparable outcomes. This reveals to us that the impacts of botnet are past simple reputational or information misfortune.
Infusing a botnet is normally an all around idea and vital methodology taken by the programmer. The procedure as a rule begins by contaminating at least one frameworks, these frameworks are then capable to reproduce the malevolent code on to different machines and in the long run cross the limits of the system to spread the disease to a more extensive and worldwide zone. So as to contaminate one framework, the aggressor needs to depend on different methods for interruptions. Commonly utilized strategy is to bait a program to a site facilitated with vindictive JavaScript code or a page written in comparative low level scripting language, for example, python. This content is simply a bootstrap, which executes and makes a stealth asset space on the machine. The content at that point interfaces with at least one site pages of a similar site, which contain the genuine payload of a botnet. The payload documents are then downloaded and held covered up under a stealth space. This payload contains every one of the modules clarified above, which assume responsibility for the machine, and the machine can be said to be contaminated now. Improved botnets don’t require the machine to be rebooted, and are fit for transforming the machine into a zombie the minute those are downloaded. Another well known infusion technique is to put the botnet malignant code as installable documents on a USB drive, and infuse the code on a machine which permits simple physical access and is powerless or uncertain. There are not many propelled techniques, for example, driving client to run a content sent as a connection, or conceal the code in a music document and appropriate it utilizing distributed offers.
The procedure referenced above is normally conceivable when enough safety efforts are not set up. For instance, a machine not running antivirus programming, or running with stale antivirus definitions can fall prey effectively. Correspondingly an un-fixed or inappropriately fixed framework or system can uncover a great deal of vulnerabilities to be misused. If there should be an occurrence of system border resistance, leaving security gaps in a firewall setup help decline the circumstance. With respect to servers, executing uncertain approaches or measures which don’t solidify the server working framework or leaving application misuses unfixed, can cause the harm. While managing Linux distros, adventures, for example, support floods and remote order execution are typically entered. Common simple strategies, for example, sending phishing messages, spyware connections and so forth, are utilized to expand the spread. It is essential to recollect that tainting one machine in a system is sufficient, in light of the fact that that machine going about as a zombie, can undoubtedly duplicate the botnet code to different machines in a similar system.
| Types Of Botnets |
Purpose |
| DoSBot | DoS and Distributed DoS assault utilizing Layer 3 to 7 protocols |
| SpamBot | Email spamming by gathering address books |
| BrowseBot | Accumulate client’s perusing patterns and feed into commercial system |
| AdSenseBot | Same as BrowseBot however focused to Google adsense |
| ChatBot | Gather talk transcripts to discover client’s visiting patterns |
| idBot | Gather userid and secret word data |
| CCBot | Gather credit card data from web based business entryway screens |
| PollBot | Control online surveys implied for items and administrations |
| BruteForceBot | Assault sites with TCP and application layer assaults |
| NetBot | Assault systems utilizing Layer 2 and 3 conventions |


